I recently picked up a few Yubikeys and after rolling them out I realised the security key space has matured quite a bit since the last time I took a look. I've put together a summary of the common standards, what to expect from each plus some buying tips.
When thinking about two-factor (2FA) or multi-factor (MFA) authentication it’s important to remember that each additional factor we add to our authentication flow should be a different type. There are three main types of authentication to consider:
- Something you know (passwords, security questions)
- Something you have (phone, email, authenticator app)
- Something you are (fingerprint, face scan)
Let's take a look at some common authentication mechanisms we might use for online services.
OTP
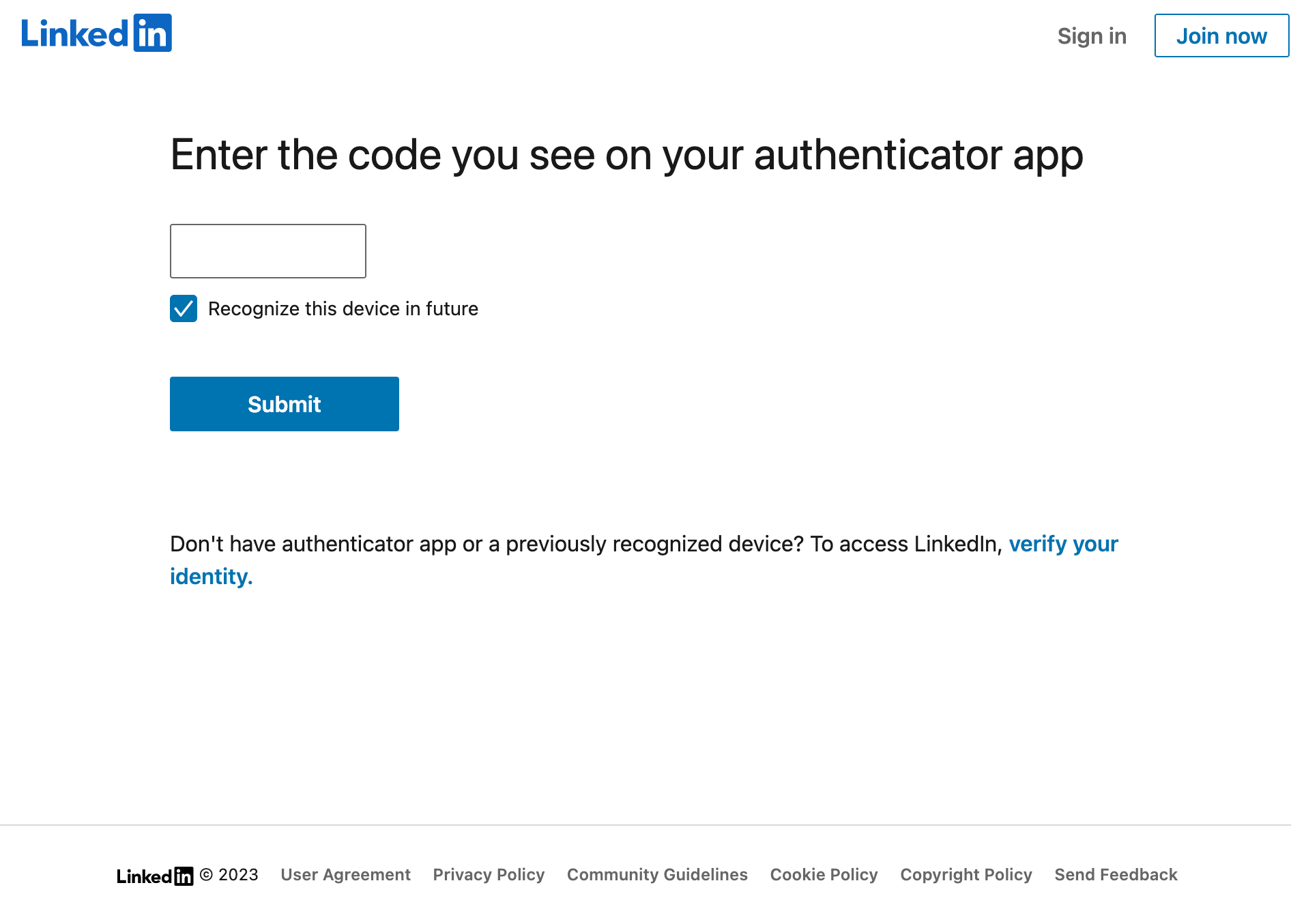
OTP or One Time Password refers to a uniquely generated code that you’re prompted to enter after your username and password. They can be generated by an application (like Google Authenticator) or sent to you via a text message or other means. They act as a second factor of authentication (something you have) in addition to your username and password (something you know).
WebAuthn
WebAuthn is a standard published by the FIDO alliance which allows security keys to be natively integrated into a website's authentication flow. It supports a range of security key functionality, most importantly U2F and FIDO2 which we'll explore below. The big win with U2F and FIDO2 is that it makes you resistant to phishing attacks since your key will only offer accounts valid for the URL of the site you're browsing.
FIDO U2F
Also referred to as U2F or CTAP1.
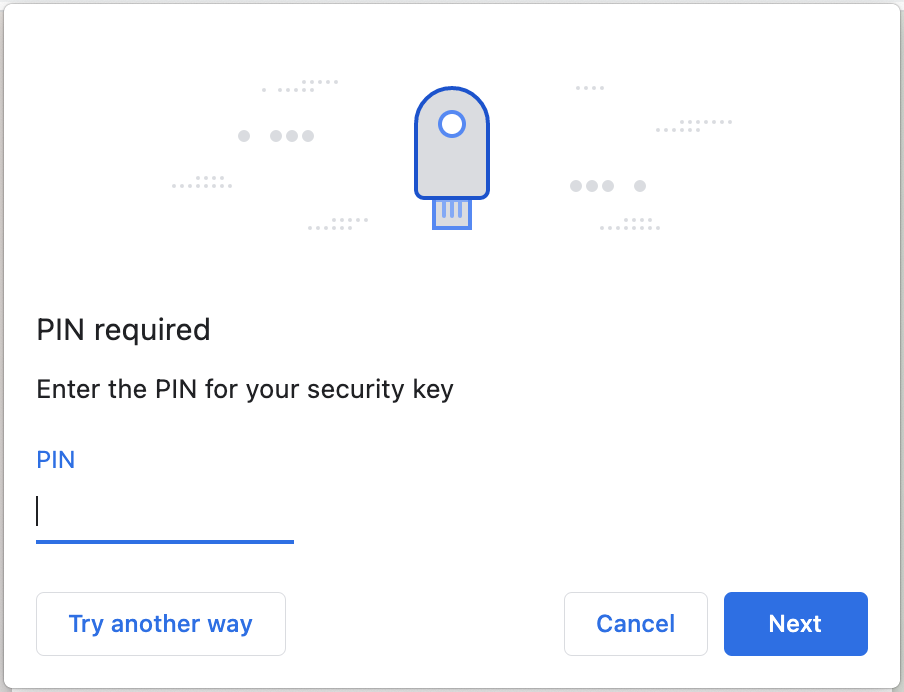
FIDO U2F or FIDO Universal 2nd Factor is a standard that offers a more convenient experience than one-time passwords. Instead of entering a generated code after your username and password, you replace the generated code with a security key (something you have). If the key is protected by a pin (something you know), simply unlock it and touch the pad to have the key cryptographically prove your second factor of authentication to the website.
U2F originally had its own API integrated into web browsers however this has since been deprecated. Support for U2F continues under the WebAuthn API. There was also a branding change from U2F to FIDO U2F, although they’re referred to interchangeably.
FIDO2
Also referred to as CTAP2.
FIDO2 is the FIDO Alliance’s extension of U2F which maintains the strong two-factor authentication offered by U2F while also supporting additional features such as passwordless sign-in. The user experience is similar to the U2F flow, however, FIDO2 takes things one step further by allowing a security key to replace your username and password at login!
Passwordless sign-in is usually implemented with an alternative sign-in button somewhere on the login page. Instead of entering your username and password, click the security key link and you'll be prompted to enter the pin and touch the top of your security key. Once this is done you'll get a list of valid accounts for the website you're currently browsing.
PIV
PIV or Personal Identity Verification is certificate-based authentication. It's the least relevant to the consumer web and has its strength in computer and corporate authentication. That said as a consumer it can be used to enhance the security of your computer logon so I kept it in here.
PIV is stereotypically what you would see in a movie from characters that are working for a government agency. They wear ID badges around their necks that can also be used to log in to their computers. It works by storing a certificate on the swipe pass and protecting it with a PIN code. The swipe pass is something you have and the PIN is something you know. This means someone would need to steal your physical security key and know the accompanying pin to unlock it before they get access to your account. Also, since the pin is tied to the security key, there's less chance of someone stealing your password by looking over your shoulder as you enter it.
Risks
Get ready for this sentence... Security keys keep their secrets secret by only allowing secrets to be saved and never copied! When a security key generates a one-time password or interacts with a website using FIDO2, the underlying secret used to generate the output is never revealed. "Great, I'm protected!" I hear you say, yes but now you can't back up your security key. Solution? Buy two! No, seriously.

If you buy two, then you can register each key individually so if you lose or break one, you can still log in to your account and remove it. Ideally, this prevents you from relying on less secure authentication methods as a backup that might be exploited.
When you're shopping around, don't forget to check the feature set of each security key! Not all brands and models have the same functionality. For example, at the time of writing the "Security Key" line of Yubikeys support U2F and FIDO2 but not OTP. This may be a problem if you're looking for coverage of some accounts that offer OTP but not U2F or FIDO2. Other considerations include supported connectivity (NFC is useful to authenticate mobile apps on the go) and the number of secrets each key can hold (this limit may differ for each function).
All in all, security keys are pretty cool tech. That said, they're not cheap so make sure you've done your research before locking in a purchase.
